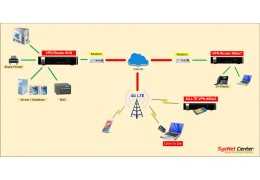
Review ทดสอบใช้งาน Reyee RG-EG406XS Router, Internet Throughput, Loadbalance, เก็บ Log Internet ตาม พรบ, L2TP...


Review ทดสอบใช้งาน Reyee RG-EG406XS Router, Internet Throughput, Loadbalance, เก็บ Log Internet ตาม พรบ, L2TP...


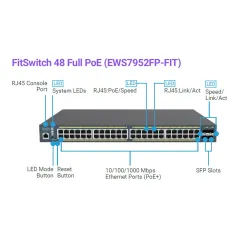


EWS7952FP-FIT
Engenius EWS7952FP-FIT FITSwitch Managed Gigabit POE Switch 48-Port, 4 SFP Port, จ่ายไฟ POE 48 Port มาตรฐาน 802.3af/at สูงสุด 740W รองรับการ Managed ผ่าน Controller
สอบถามข้อมูลสินค้าเพิ่มเติม
LINE ID: @sysnet โทร: 02 102 4284
Click ต้องการใบเสนอราคา
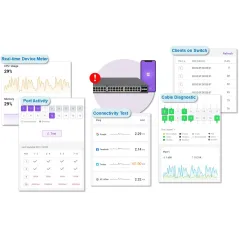
EnGenius Fit Managed Switch Datasheet
EnGenius Fit Management Datasheet
Review Engenius Fit โซลูชั่น Access Points และ Switches
Product Highlight
EWS7952FP-FIT L2 Managed POE Switch Technical Specifications | |
| Port Standards | 802.3 10Base-T Ethernet 802.3u 100Base-TX Ethernet 802.3ab 1000Base-T Ethernet 802.3x Full-Duplex Flow Control |
| Network Port Gigabit Ethernet Ports | 48×10/100/1000 Mbps Ports |
| Network Port – SFP Ports | 4 SFP Ports |
| Switching Capacity | 104Gbps |
| SDRAM | 256MB |
| Flash Memory | 32MB |
| PoE Capable Ports | Ports 1-48 |
| Total PoE Budget | 740W |
| Power Source | 100 to 240 VAC, 50/60Hz |
L2 Features | |
| Network Management | EnGenius FITCloud FITCON Local Web GUI |
| MAC Address Table | 16K |
| Jumbo frame size | 9K |
| Multicast Group | Max 256 groups |
Physical Interface | |
| LED Indicators | Power LED Fault LED PoE Max LED LAN Mode LED PoE Mode LED |
| Ports | Link/Activity/Speed (per Ethernet port) Link/Activity/Speed (per SFP slot) |
Wireless Management Features | |
| Deployment Options | Stand-Alone (Individually Managed) FitXpress FitController |
Environmental & Physical | |
| Temperature Range | Operating: 32°F to 104°F (0°C to 40°C) |
| Humidity (Non-Condensing) | Operating: 5% – 95% |
Dimensions & Weight | |
| Device Dimensions & Weights | Weight: 10.5 lbs. (4.76 kg) |
| Package Contents | 1x FIT Managed Switch 1x Quick Installation Guide 1x Power Adapter 1x Power Cord 1x Wall Mount Kit 1x Ground Screw Set |
Software Lists of Layer 2-Plus Managed Switches | |
Layer 2 Features | DHCP Snooping DHCP Relay DHCP Option 82 PoE (Power over Ethernet) EEE (Energy Efficient Ethernet) Link Aggregation STP (Spanning Tree Protocol) LBD (Loopback Detection) Jumbo Frame MAC Address Table LLDP (Link Layer Discovery Protocol) IGMP Snooping MLD Snooping Multicast Filtering |
VLAN Features | 802.1Q VLAN PVID (Port VLAN ID) Voice VLAN MAC based VLAN* Protocol VLAN* Dynamic VLAN assignment * Available through future firmware upgrade. |
Quality of Service | Quality of Service Class of Service (CoS) CoS Mapping Weighted Round-Robin (WRR) Bandwidth Management |
Security | Radius Server 802.1X Authentication Protocol 802.1x Port-based Access Control MAC-Based Port Security (MAC-based Access Control) Authenticated Host Guest VLAN VLAN Tag Radius VLAN Assignment Management VLAN Storm Control Port Isolation DoS Attack Prevention Access Control List Login Authentication Control |
Management | Account Multi-Privileges Management HTTPS SSH Tunnel SNMP & MIB Remote Network Monitoring (RMON) PoE Management PD LifeGuard Port Mirroring Syslog Ping Trace Route Cable Diagnostics Dual Image Firmware Update Configuration Backup/Restore Reboot/Reset |
ประกัน | 5 ปี |
ยังไม่มีการ review กรุณาเขียน review
ไม่มีคำถามที่ใช้ได้ ถามคำถามของคุณ

EWS7952FP-FIT
Engenius EWS7952FP-FIT FITSwitch Managed Gigabit POE Switch 48-Port, 4 SFP Port, จ่ายไฟ POE 48 Port มาตรฐาน 802.3af/at สูงสุด 740W รองรับการ Managed ผ่าน Controller
check_circle
check_circle